Advanced BQT Electronic Safety And Security Equipments for Residences and Services
Advanced BQT Electronic Safety And Security Equipments for Residences and Services
Blog Article
Maximizing Business Protection: The Ultimate Guide to Electronic Safety Solutions
In the fast-paced and ever-evolving landscape of company safety, the dependence on electronic safety and security solutions has actually ended up being vital for safeguarding useful properties, private details, and maintaining operational connection. In this guide to electronic safety and security services, we will explore the most recent patterns, cutting-edge innovations, and ideal techniques to strengthen your organization against potential dangers and vulnerabilities.
Importance of Electronic Safety And Security Solutions
When taking into consideration the defense of properties and delicate info, the relevance of digital safety solutions can not be overemphasized. In today's interconnected globe, where cyber risks are frequently developing and coming to be more sophisticated, companies should focus on implementing durable electronic safety and security procedures to protect their data and operations. Digital security solutions include a large range of modern technologies and techniques created to defend against unauthorized accessibility, information breaches, malware, and various other cyber risks.
Among the crucial benefits of electronic safety services is their ability to offer real-time monitoring and danger discovery. BQT Electronic Security. Through devices like invasion discovery systems, firewall softwares, and safety info and event management (SIEM) systems, organizations can proactively identify and react to safety occurrences prior to they escalate right into major violations. Additionally, digital security remedies aid guarantee compliance with market guidelines and standards, safeguarding companies from possible lawful and monetary consequences
Kinds Of Electronic Security Solutions
Offered the vital relevance of electronic safety and security services in safeguarding companies versus cyber hazards, it is vital to explore the various kinds of electronic security systems offered to improve defense and strength. Among the most common types of electronic safety systems is the firewall software, which acts as an obstacle in between a company's internal network and exterior networks, removing possibly harmful data. Invasion Detection Equipment (IDS) are additionally crucial, as they keep track of network web traffic for dubious activity and alert managers to possible dangers. In addition, companies typically count on security innovations to secure sensitive data both at rest and in transit. Accessibility control systems, consisting of biometric viewers and keycard access, help regulate entrance to physical spaces and safeguard properties. Video clip surveillance systems play a role in surveillance and recording tasks within and around the properties. By using a combination of these digital protection systems, services can develop a durable defense versus various safety dangers.
Executing Access Control Procedures

Furthermore, access control measures can be incorporated with security systems to keep track of and videotape individuals' activities within secured areas. This combination enhances safety and security by supplying an extensive summary of who is accessing certain places at any given time. Furthermore, access control systems can be configured to limit access based upon time, area, or specific qualifications, allowing companies to customize safety and security methods according to their certain demands.
Cybersecurity Best Practices
To enhance general security position, applying durable cybersecurity ideal practices is vital in guarding digital possessions and information stability. One fundamental technique is ensuring routine software program updates throughout all tools and systems to spot susceptabilities promptly. Utilizing strong, one-of-a-kind passwords and applying multi-factor authentication includes layers of defense versus unapproved access. Conducting regular protection audits and assessments assists recognize weak points and areas for improvement. Employee training on cybersecurity understanding is critical our website in preventing social design attacks and making certain a security-conscious workforce.
Establishing an extensive case feedback strategy allows swift and reliable feedbacks to security violations, minimizing possible damage. Securing delicate information both in transit and at rest offers an additional obstacle versus data violations. Carrying out accessibility controls based upon the principle of least advantage limits the exposure of critical systems and details to just those who need it for their duties. Regular back-ups of information ensure that in case of a ransomware strike or information loss, crucial info can be recouped. Embracing an aggressive approach to cybersecurity through continual surveillance and danger intelligence helps identify and minimize possible threats prior to they rise. By integrating these best techniques right into cybersecurity methods, services can fortify their defenses versus advancing cyber threats.
Surveillance and Monitoring Solutions
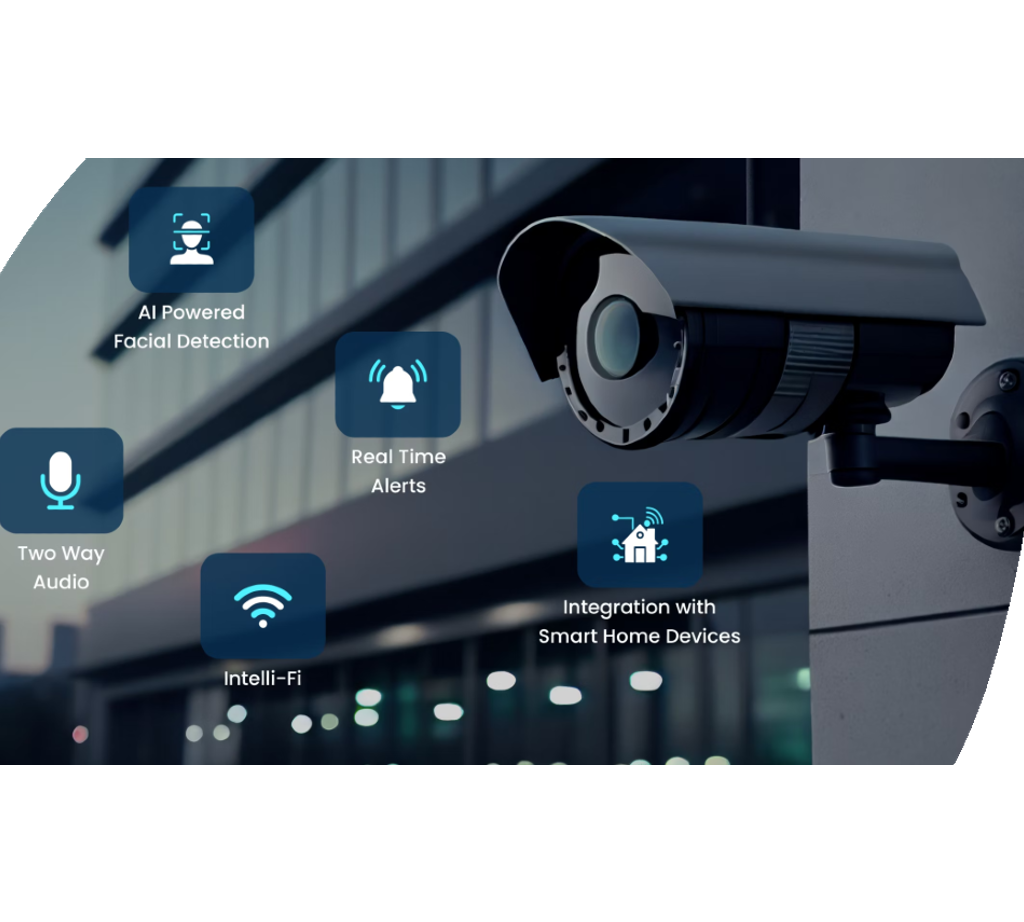
Video security remedies provide remote surveillance capabilities, permitting accredited employees to watch on the facilities also when off-site. In addition, progressed functions like activity discovery, face recognition, and certificate plate acknowledgment boost the general protection stance of the organization. Integrating monitoring systems with security system and gain access to control better strengthens the safety and security facilities, allowing an aggressive feedback to possible safety and security violations.
Conclusion
In verdict, digital security solutions are vital for maximizing organization protection. By applying gain access to control steps, cybersecurity best methods, and surveillance and monitoring solutions, businesses can successfully safeguard their possessions and info. It is very important to buy the best digital safety and security systems to ensure the safety and security and security of the company. Remember, avoidance is essential in securing against potential threats and susceptabilities (BQT Locks). advice
Report this page